A Mirai-based botnet named Gayfemboy has become a global cybersecurity threat, infecting over 15,000 devices daily by exploiting a combination of weak security practices, known vulnerabilities, and a critical zero-day flaw in industrial routers.
Discovered by Chainxin X Lab, the botnet targets IoT devices and industrial routers, including those manufactured by Four-Faith, Huawei, and ASUS. Researchers have linked its rapid spread to the exploitation of CVE-2024-12856, a previously unknown vulnerability in Four-Faith routers.
The botnet’s operators employ advanced techniques, leveraging brute-force attacks on Telnet passwords and customized UPX-packing to conceal their payloads. According to VulnCheck, the vulnerability at the center of these attacks has been actively exploited since November 2024, allowing attackers to execute remote commands and take control of devices.
The growing threat shows the risks of unpatched devices and poor cybersecurity practices in industrial and IoT ecosystems.
The Four-Faith Router Vulnerability
The Four-Faith router vulnerability, identified as CVE-2024-12856, is a command injection flaw that allows attackers to execute arbitrary commands through the router’s apply.cgi endpoint.
It relies on default administrative credentials to bypass authentication and gain control of the device. VulnCheck describes the flaw as “an issue that provides attackers with remote access, enabling them to launch malicious payloads and disrupt targeted systems.”
The exploitation of this vulnerability has primarily affected the F3x24 and F3x36 router models, which are commonly deployed in industrial environments.
Chainxin X Lab discovered that the botnet not only targets these devices but also leverages vulnerabilities in other routers, including Neterbit models, to expand its reach. Additionally, it has been observed exploiting smart home devices such as those from Vimar, using unknown vulnerabilities to propagate further.
The Methods Behind the Spread
The Gayfemboy botnet’s operators use a mix of established and advanced techniques to infect devices and maintain their network. One of the primary methods is brute-forcing Telnet credentials.
Telnet, a legacy protocol still widely used in many IoT devices, is often left unsecured with default usernames and passwords, providing an easy entry point for attackers. Once compromised, the devices are grouped based on their hardware characteristics and controlled via a command-and-control (C2) infrastructure.
Another key aspect of the botnet’s approach is the use of customized UPX-packing. UPX, or Ultimate Packer for Executables, is a compression tool that reduces the size of executable files. Malware developers often modify UPX signatures to evade detection by antivirus software, and Gayfemboy operators have implemented this technique to great effect.
The botnet also relies on over 20 known vulnerabilities in various devices. For example, it exploits CVE-2017-17215 in Huawei routers and CVE-2024-8957 in Pan-tilt-zoom (PTZ) cameras to compromise their systems. This arsenal of vulnerabilities, combined with its ability to rapidly integrate new exploits, has made Gayfemboy one of the most adaptive and dangerous botnets in operation today.
Retaliatory Behavior and Global Targets
The botnet has shown an aggressive stance toward researchers. In one instance, Chainxin X Lab registered unused command-and-control domains associated with the botnet to observe its activity.
In response, Gayfemboy operators launched direct DDoS attacks against these domains, disrupting the researchers’ infrastructure. This behavior illustrates the sophistication and hostility of the botnet’s operators.
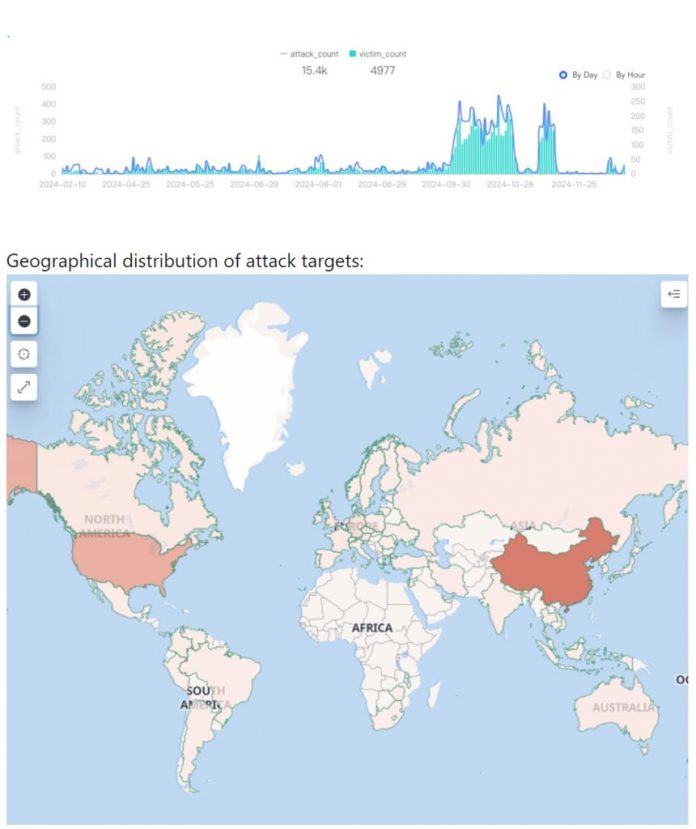
The geographic distribution of infections spans major regions, including China, the United States, Russia, Turkey, and Iran. Attack logs indicate that the botnet is capable of generating DDoS traffic exceeding 100 Gbps, overwhelming even robust defenses.
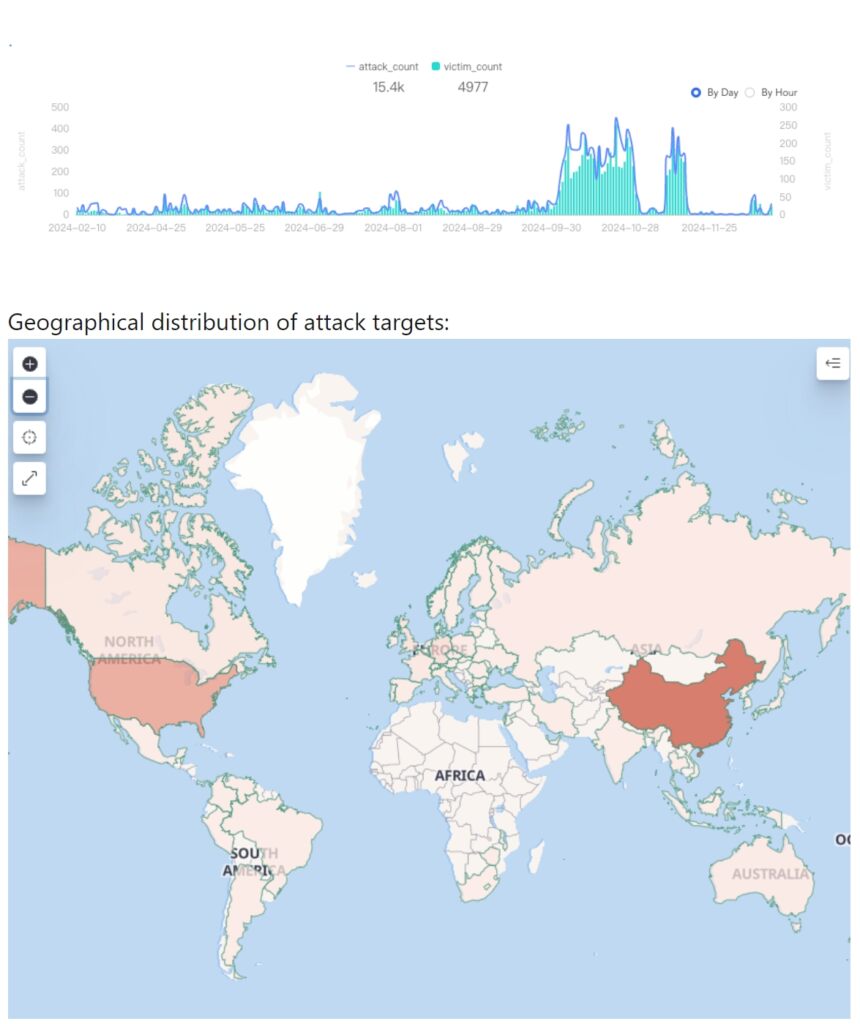

While the attacks are often brief, lasting 10 to 30 seconds, they can cause significant disruptions, particularly in critical sectors like telecommunications and industrial systems.
The Role of Industrial Routers and IoT Devices
Industrial routers like those manufactured by Four-Faith play a critical role in managing network traffic and ensuring reliable communication in sectors such as energy, manufacturing, and logistics.
The exploitation of these devices highlights a pressing issue in cybersecurity: the lack of robust security measures for devices deployed in critical environments. Smart home devices, though smaller in scale, represent an equally vulnerable category, with attackers leveraging their ubiquity to amplify their operations.
As Chainxin X Lab noted, “The botnet targets hundreds of different entities each day. The attack targets are spread across the globe, covering various industries. The main attack targets are concentrated in regions such as China, the United States, Germany, the United Kingdom, and Singapore.”
Mitigation Strategies
The cybersecurity experts emphasize the importance of securing IoT and industrial devices through proactive measures. These include regularly updating firmware, replacing default credentials, and implementing network segmentation to isolate vulnerable devices. Organizations are also advised to deploy monitoring tools capable of detecting anomalies and responding to threats in real-time.
VulnCheck recommends that affected users immediately apply patches provided by manufacturers or, where unavailable, disable exposed endpoints and adopt stricter access controls. As cyber threats evolve, industry stakeholders must prioritize security to prevent further exploitation of these devices.